WireGuard - Next Generation VPN
This guide will help you get a basic WireGuard configuration up and running easily for proof of concept or evaluation purposes.
Quick Start
WireGuard VPN Server on Telco T1
This VPN configuration makes it as if your client device(s) is/are connected to the LAN or WiFi of the T1.
0. Prerequisite
You need a public IP address, which usually incurs an additional fee from your mobile network operator. Additionally, DDNS can make it easier for you if you do not have a static public IP address. See this guide for setting up DDNS on TelcOS Melaleuca.
1. Set up the Server
On the T1, go to Network > Interfaces > Add New Interface and create one with the WireGuard VPN protocol. In our example, the interface is named wg1
Note that the key and port are both pre-filled for you, so skip these unless you have your own key you want to use.
Set the IP address via the dropdown menu. By default 192.168.200.1 is there for you to select.
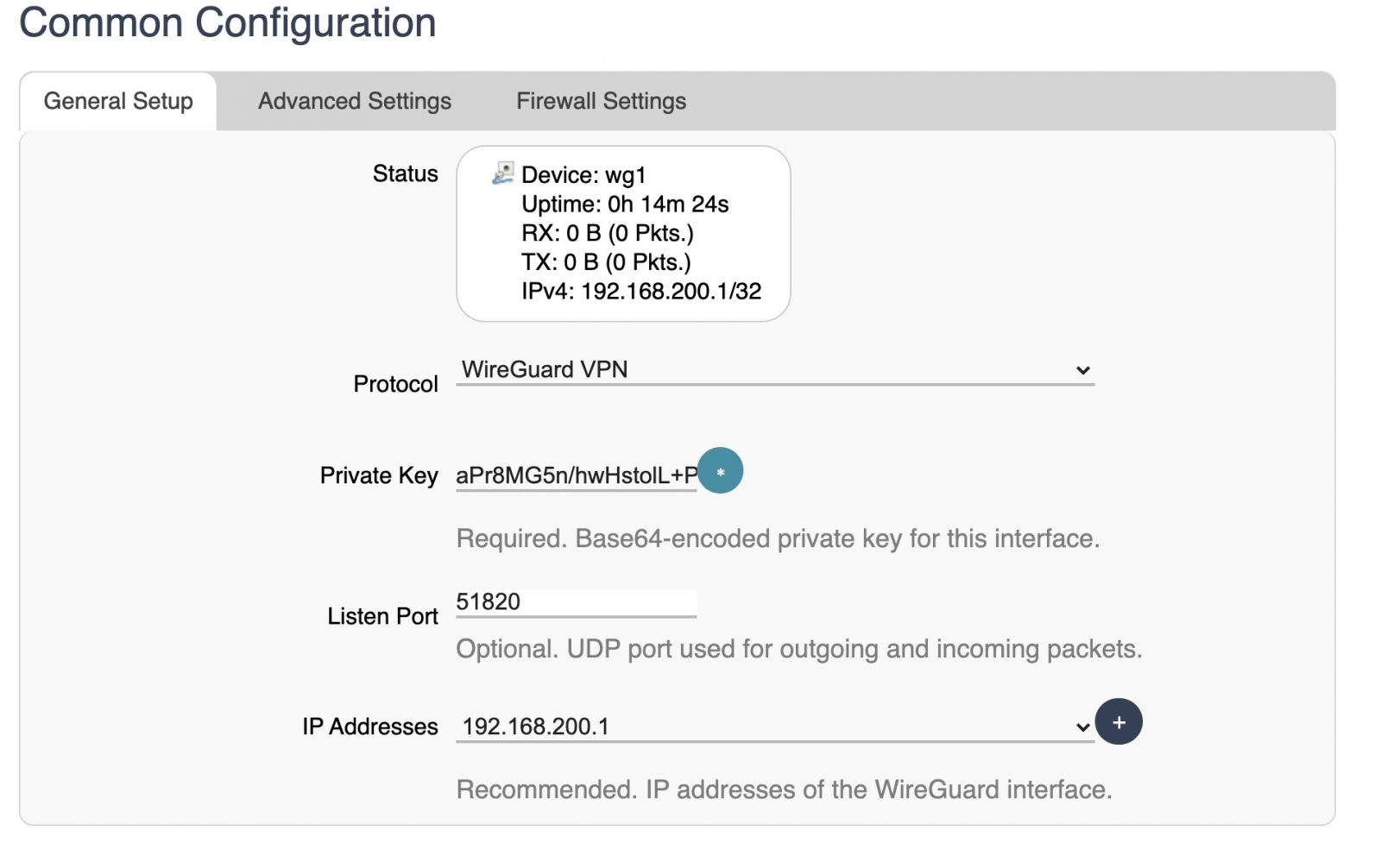
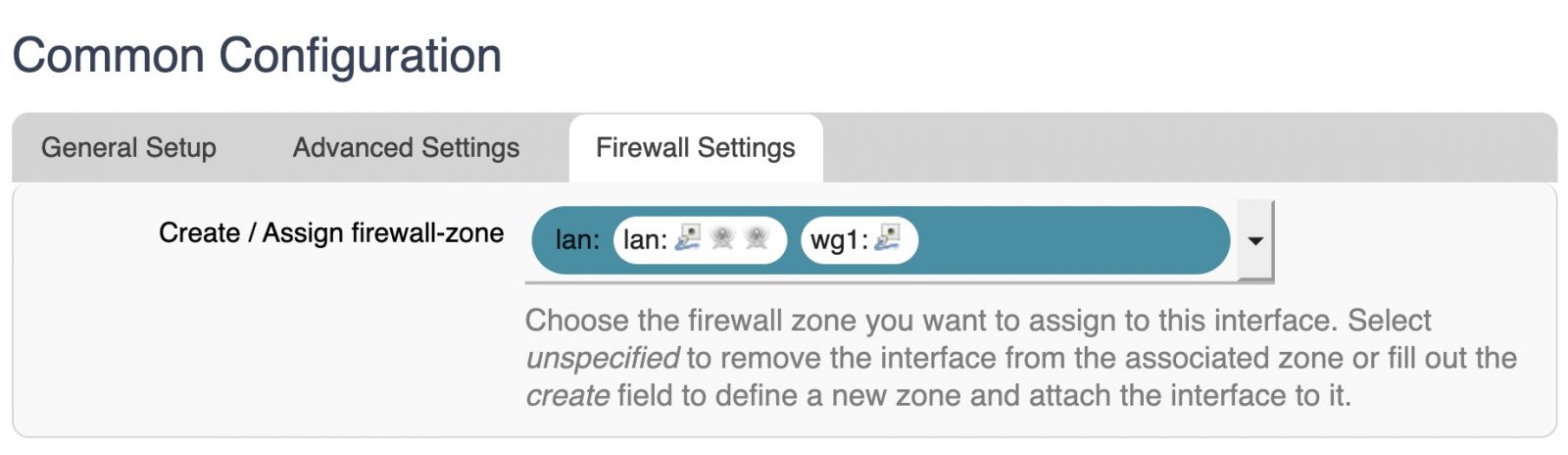
Set the Firewall Zone to LAN
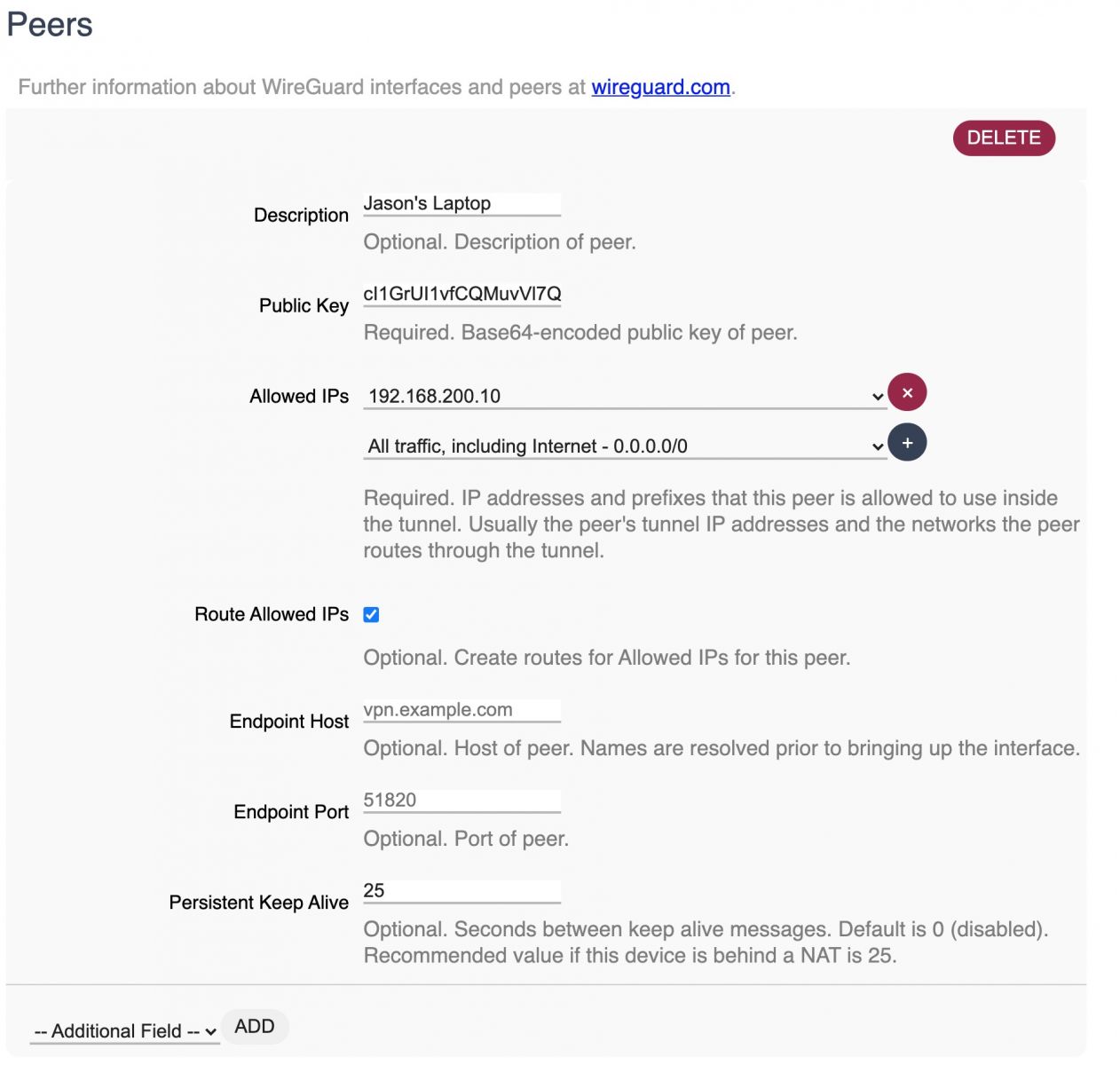
2. Add a client
- Your client computer will need to have WireGuard installed.
- Generate the WireGuard configuration file for this client on that computer. This can be done by opening the WireGuard app and creating a new "Tunnel".
- Enter the Public Key for that client into the Public Key field of the Peer you are adding on the T1.
- Tick the Route Allowed IP's box
- Add an optional Description field
3. Finish Setting up your Client.
Finally, on your client add the Telco T1 as a peer, using the T1's public key and public IP address or DDNS hostname as the endpoint, remembering to include the :51820 port at the end.
Your configuration file on the client should resemble the following:
[Interface] PrivateKey = notMyR3AlW1reGu4rdKey= Address = 192.168.200.20/32 DNS = 192.168.200.1, 1.1.1.1 [Peer] PublicKey = notMyR3AlW1reGu4rdKeyE1th3r= AllowedIPs = 0.0.0.0/0 Endpoint = your.Public.IP.or.DDNS.hostname.net:51820 PersistentKeepalive = 25
Now, with WireGuard running on the server, start up the WireGuard connection on your client. You can now access the Telco T1 via the VPN, and should have access to anything connected to the Telco T1's LAN. This VPN configuration makes it as if your client device is connected to the LAN or WiFi of the T1.
Tip
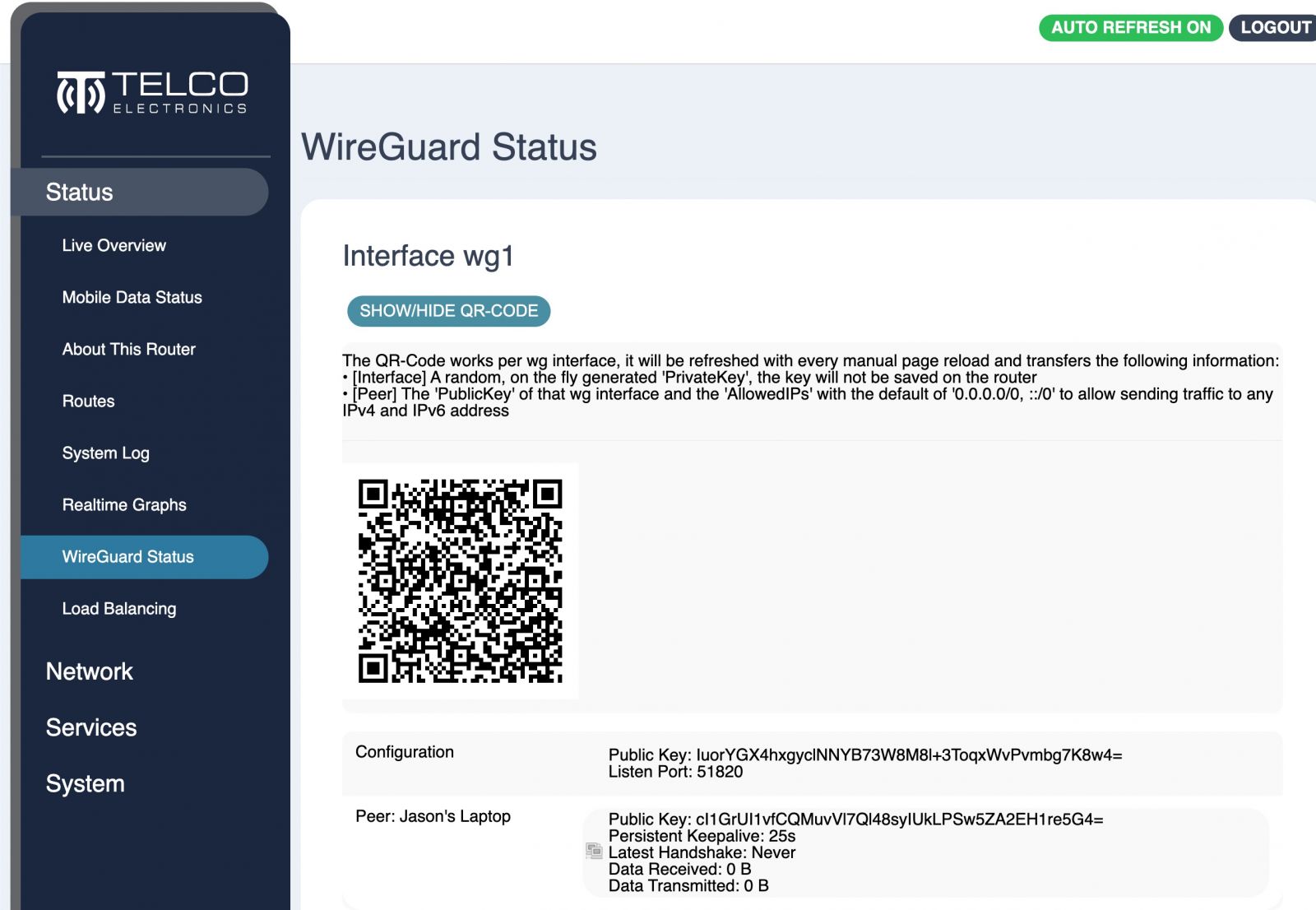
If your client is a mobile phone, go to the WireGuard Status page, then simply open the WireGuard app on your phone and scan the QR code to get the majority of the T1 Server configuration onto your phone. And the right endpoint address to the Peer on your phone. You can then paste the public key from your phone onto the T1 by editing the WireGuard interface from your phone.
WireGuard In Depth
About WireGuard
WireGuard, is a great choice for a VPN because it is secure by default, and is much simpler to set up than other VPNs. With its high performance and low resource overhead, WireGuard enables VPN connectivity for devices that may be roaming in and out of areas with poor signal availability. WireGuard scales easily, which is why it's perfect for a simple, secure point to point link, a road warrior setup for a small business, or a network with thousands of hosts.
The following serves as a guide for setting up WireGuard as a "server" on an Ubuntu Linux machine, and connecting a T1 to it, in order to help you integrate WireGuard into your ICT infrastructure.
Requirements
1. Server with Public IP Address
We tested the server installation on an Ubuntu 16.04 LTS server with IP forwarding enabled, but the OS really shouldn't matter. All you need is a Linux server with IP forwarding enabled and a public IP address.
2. WireGuard Client Software
We won't go into the details for how to install WireGuard on your host because this is well documented for all platforms here: https://www.wireguard.com/install/
TelcOS Melaleuca includes WireGuard by default. To create a new WireGuard instance, just make a new Network Interface using the WireGuard protocol. We will show you how to do that and set it up later.
Steps
1. Create your keys
The server and all clients require a pair of keys: public and private keys. All devices will know two things: their own private key, and all public keys of every other device in the tunnel. To generate keys, just run these commands any time you need to make a new keypair to identify a new peer. (Remember, in WireGuard even your server is a peer).
wg genkey | tee privatekey | wg pubkey > publickey
When you run this command, two files will be created in the current working directory which contain the public and private keys in text format. You will use the contents of these files later. The files can be read with any text editor or with cat.
2. On the server, put something like this in /etc/wireguard/wg.conf
Note the comments in line
[Interface] Address = 192.168.200.1/24 # The WireGuard IP address of this WireGuard peer, which you can think of as a "server". Address = 192.168.0.223/24 # The IP address of the server's real NIC SaveConfig = true # Save the config if it gets updated ### Some firewall rules specific for this installation of Ubuntu to let WireGuard work and access the real NIC's networks PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o enp0s3 -j MASQUERADE; ip6tables -A FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -A POSTROUTING -o enp0s3 -j MASQUERADE PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o enp0s3 -j MASQUERADE; ip6tables -D FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -D POSTROUTING -o enp0s3 -j MASQUERADE ListenPort = 1194 # We just happen to be using the standard OpenVPN port PrivateKey = 2n345h34nsnthNotMyRealKeynsnst2h342nqjsnh= # Add peers as needed, you can even write a script to do this for you # There are QR code packages that let you enrol clients easily [Peer] PublicKey = 2ZOChMMk/PNotTheirRealKeyEither/yTUJnNA3P1Q= # The public key of this client AllowedIPs = 192.168.200.10/32 # The IP address that this client will have in the WireGuard tunnel
Choose 3a for a generic client and 3b for a TelcOS Melaleuca client
3a - Client configuration
If the client is a laptop or a mobile phone, enter this into the WireGuard client's configuration using the app for that client's OS.
Official WireGuard clients are available for Windows Mac, Android, any Linux distribution, including TelcOS; check https://www.wireguard.com/install/
[Interface] PrivateKey = 2Fu9YcNotMyRealKeymYi7fTEDe63A= Address = 192.168.200.10/24 [Peer] PublicKey = uHuaoe2HDeuCi8NotMyRealKeyQhecIIHUNAkU= AllowedIPs = 192.168.0.0/24, 192.168.200.0/24 # I want to be able to get onto both the LAN and the WireGuard networks Endpoint = 180.214.64.26:1194 # The static IP and port of the server PersistentKeepalive = 25 # This helps keep the connection alive when behind NAT
3b - TelcOS Melaleuca configuration
If the client device is a device running TelcOS Melaleuca, follow this instead:
There are two common operation modes, and two cooresponding firewall configurations.
Remote Management Config - To remotely access and manage a Telco Electronics device
- Follow all of these steps putting the WireGuard interface into the LAN firewall zone.
VPN Router Config - To allow all connected devices to use networks and resources made available by the tunnel
- Follow all of these steps putting the WireGuard interface into the WAN firewall zone.
Step 1 - Create the WireGuard interface by navigating to Network > Interfaces > and choosing Add New Interface
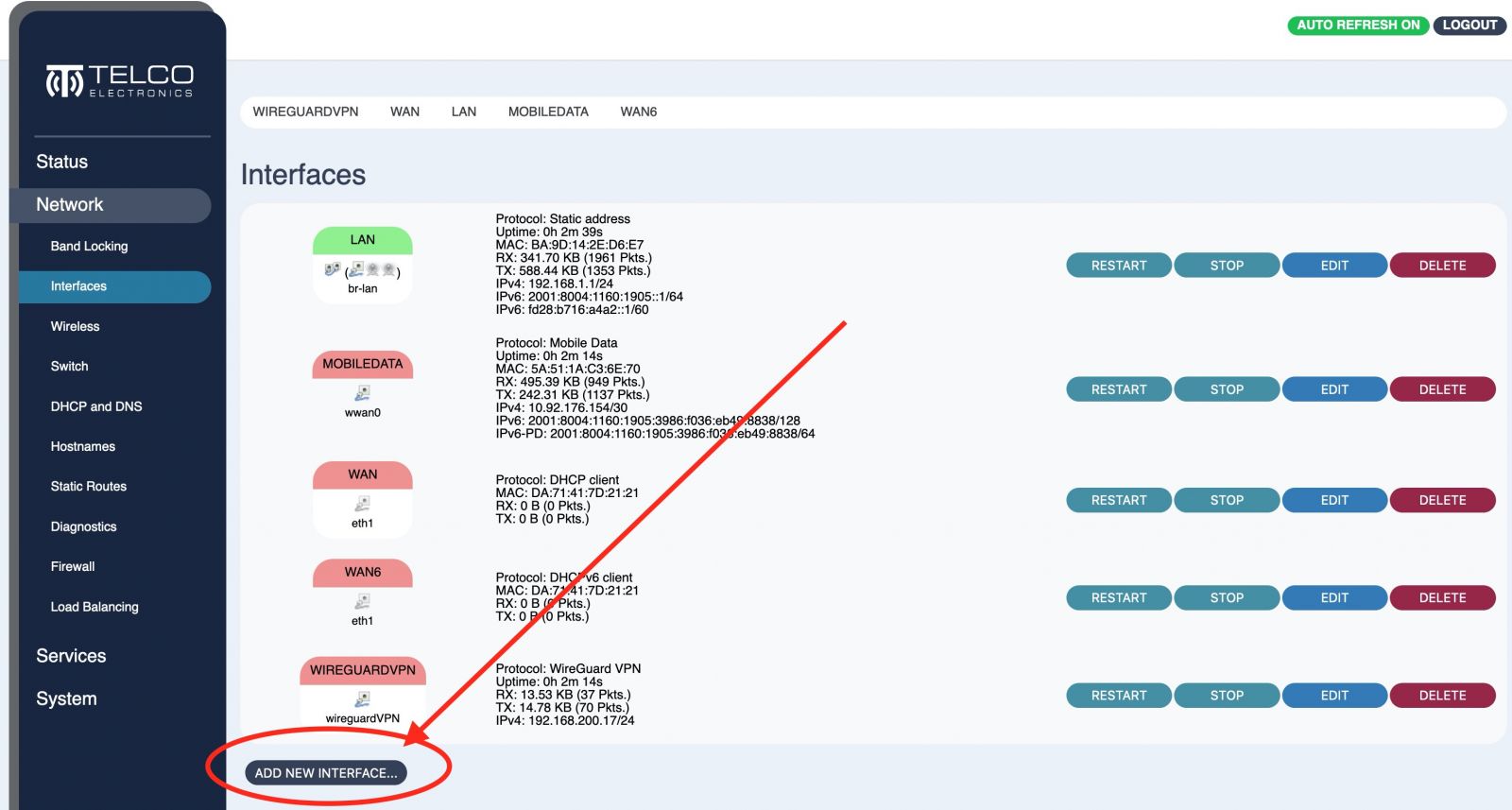
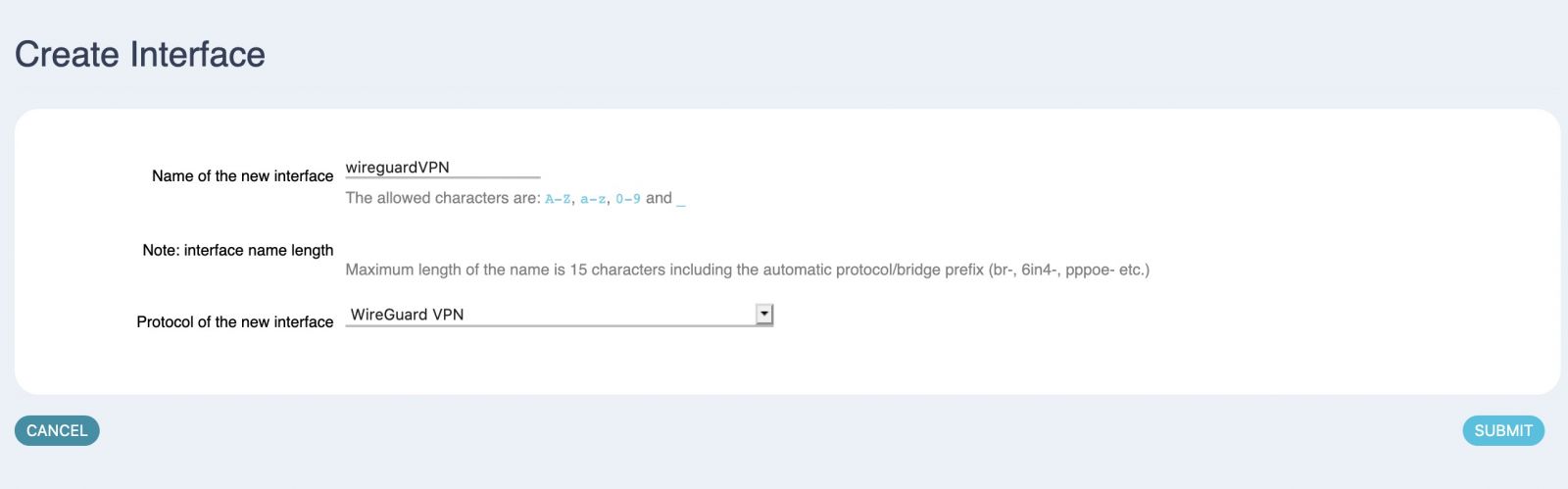
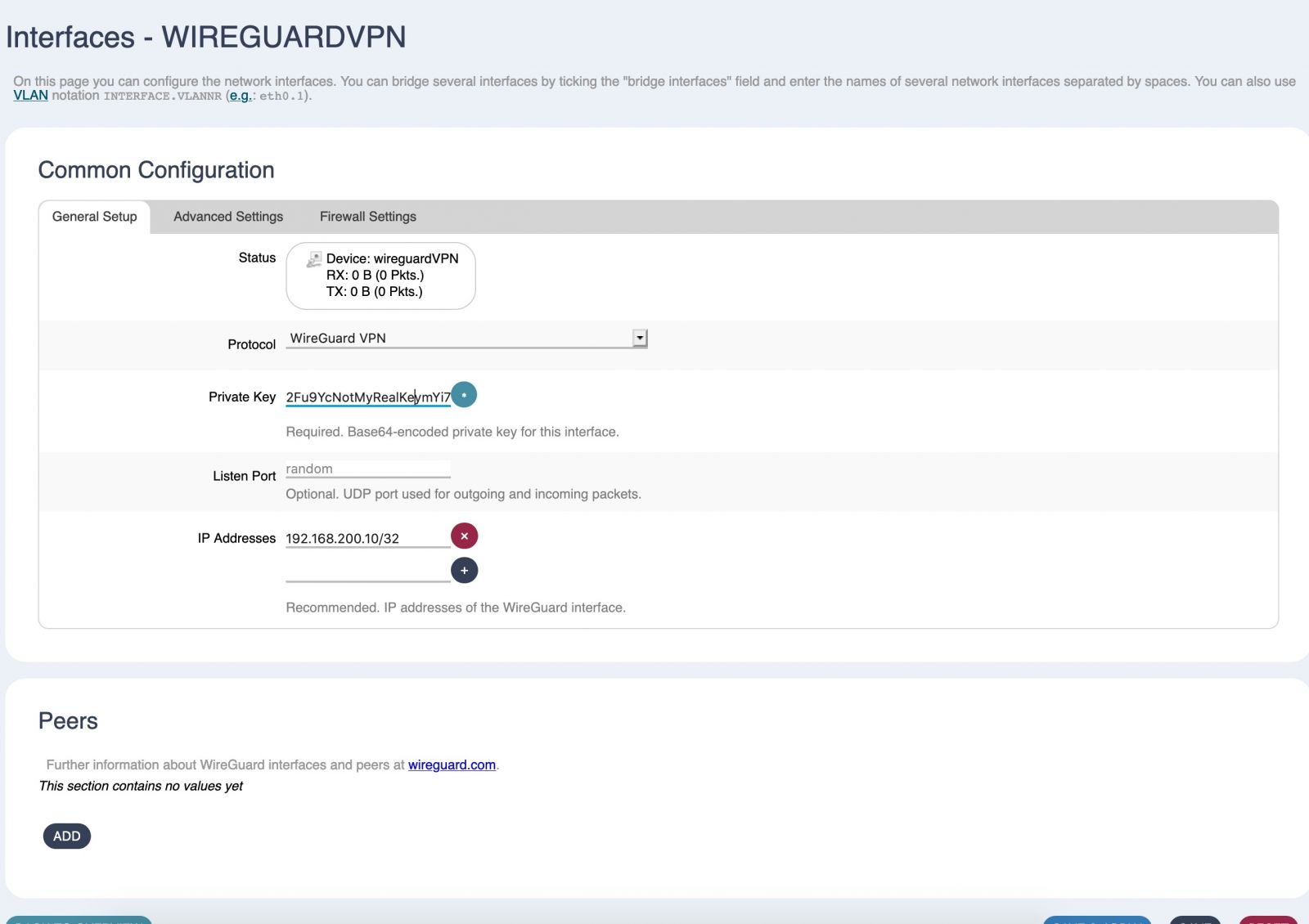
Step 2 - Enter the private key and IP address you are assigning to this Telco Electronics device.
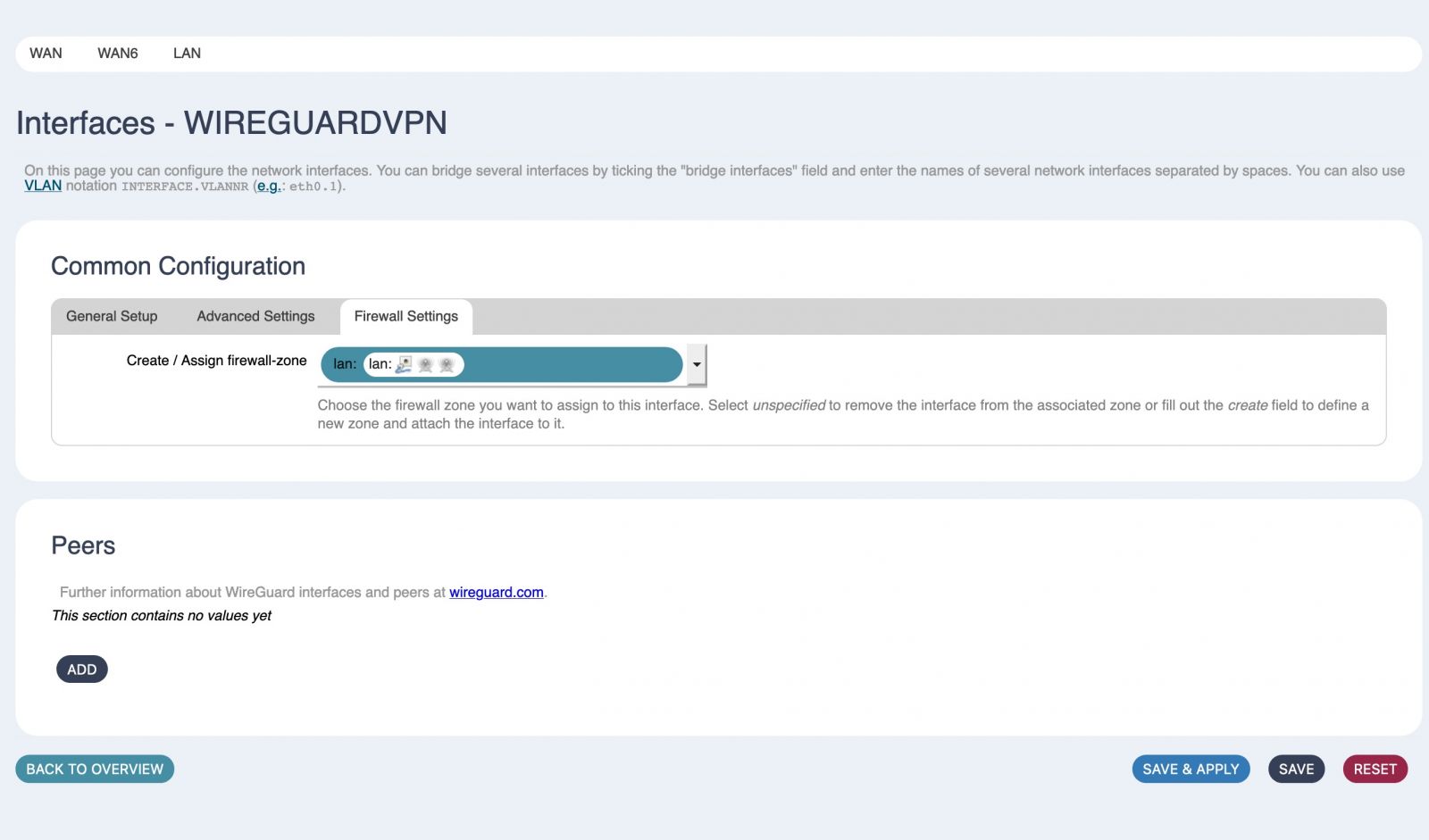
Step 3 - Add the interface to the Firewall group. See the beginning of this section for options. In this tutorial we will use the LAN group because we want to access this Telco Electronics device via the Tunnel.
Step 4 - Add the server as a Peer. Add an addional Description field if you would like to.
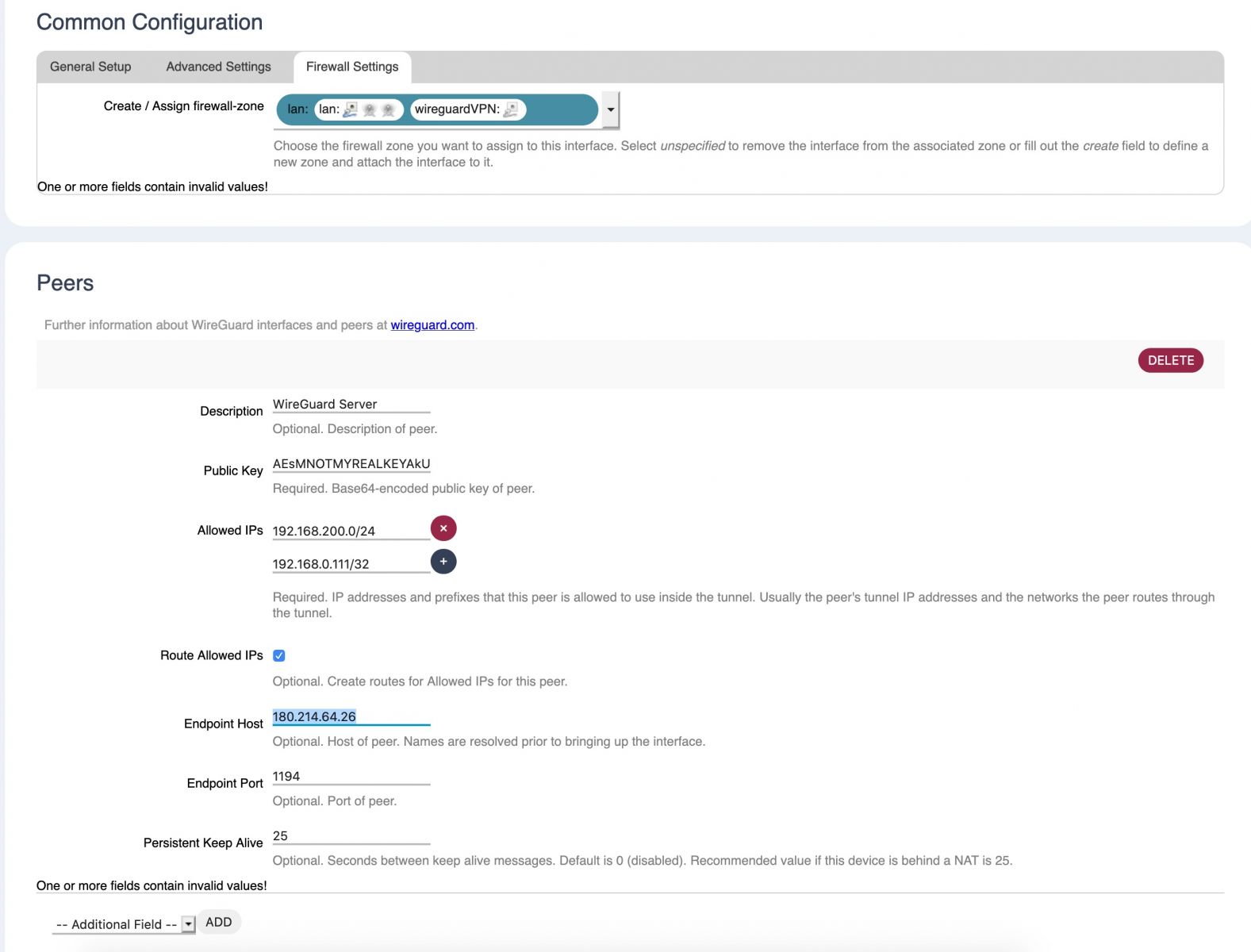
Step 5 - Reboot and if you followed along carefully everything will be working well.
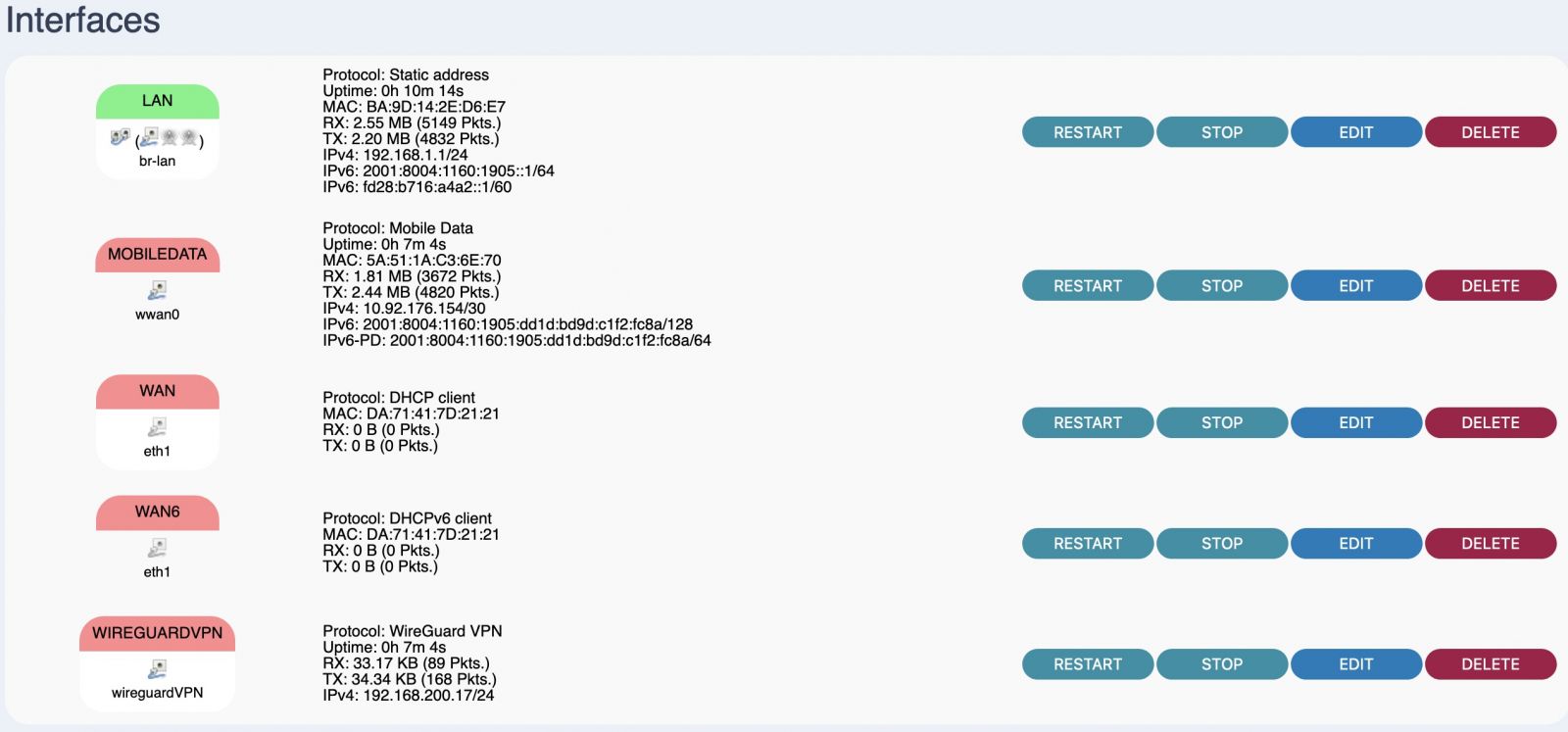
You can access and administer the WireGuard devices using their WireGuard IP address, because that interface was put in the LAN firewall zone.
If you would like any device that connects to the Telco Electronics device to be able to access networks and resources provided by the WireGuard tunnel, just add the WireGuard interface to the WAN zone as below:
Not working?
The biggest tip for beginners is to make sure you have written everything exactly as it should be in those configuration files. WireGuard controls access to a peer based on it having not only the correct ID but also the correct IP and subnet, so make sure all of those are correct. You are essentially mirrioring the configuaration of any peer to the master peer. If you are still stuck, send your config files via an enquiry and we will be happy to help you get setup.
